SEVERAL iPhone owners say they have been the target of an elaborate phishing attack that seeks to lock customers out of their Apple ID accounts.
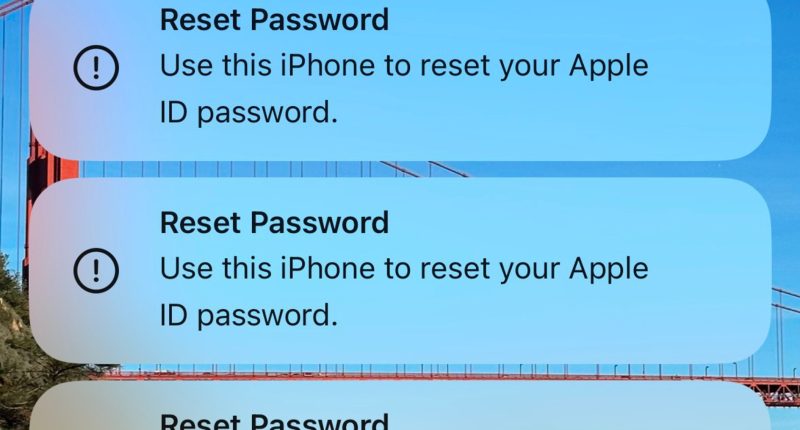
The aggressive attack takes advantage of a bug that lets cyber crooks bombard devices with alerts to approve a password change – which is then followed up by a fake call from ‘Apple Support’.
“All of my devices started blowing up, my watch, laptop and phone,” iPhone owner and AI entrepreneur, Parth Patel, told KrebsOnSecurity.
“It was like this system notification from Apple to approve [a reset of the account password], but I couldn’t do anything else with my phone.
“I had to go through and decline like 100-plus notifications.”
These notifications are Apple system alerts triggered by hackers, making them legitimate requests from a malicious sources.
READ MORE ON IPHONES
Each Reset Password request will lock an Apple device until the owner clicks ‘Allow’ to change their password or ‘Don’t Allow’.
Some may click ‘Allow’ simply to make the barrage stop.
But the hackers don’t stop there.
‘Win trust from the victim’
The bombardment of notifications is then followed up with a spoof call from ‘Apple Support’.
Most read in Phones & Gadgets
What is a spoof call?
A quick breakdown of spoof calls:
Spoof calls – or caller ID spoofing – is when a hacker intentionally copies another phone number to either disguise their identity or masquerade as another.
They are incredibly convincing, but remember: Apple typically does not make unsolicited calls.
If in doubt, call them back yourself by re-typing the legitimate number into your iPhones keypad.
Do not call them back by clicking on the potential spoof number that has rung you.
“About 15 minutes later, they call me on my number, using Caller ID spoofing of the official Apple Support phone line (1 (800) 275-2273),” Patel explained on X (formerly Twitter).
“They really emphasised this detail to win trust from the victim.
“I was obviously still on guard, so I asked them to validate a ton of information about me, before answering any of their questions…
“They got a lot right, from DOB, to email, to phone number, to current address, historic addresses…
“Despite correctly stating all of my data, the phishers thought my name was Anthony S.”
Hackers had used information gathered from various data bases and data leaks to create a profile of their victim.
Fortunately in Patel’s case, they got his name wrong.
But others might not always be that fortunate.
Final jab
This “sophisticated” phishing attack, as Patel calls it, is three-pronged – meaning hackers make a trio of bids to gain access to your device.
First, the Reset Password notification spamming, then the spoof call, and lastly: asking for your one-time password.
One-time passwords are security measures to prevent identity theft, and ensure only you can access your accounts.
You can make sure you receive one when you set up two-factor authentication on your iPhone.
When hackers try to break into your account using the ‘Forgotten Password’ ploy, a one-time password is sent to the real owner of the account.
In this instance, Patel received a one-use-only Apple ID code in his iMessages to gain access to his account.
These emergency codes are always sent with a message from Apple, which says: “Don’t share it [the code] with anyone.”
READ MORE SUN STORIES
While on the spoof call with the hackers, they asked Patel for the code.
If he had given it up, they would have been given unfettered access to his Apple ID account – and he would have lost everything in his Apple network.